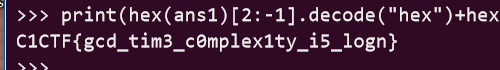
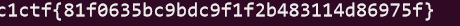
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
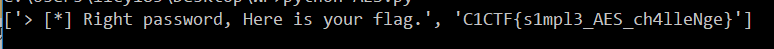
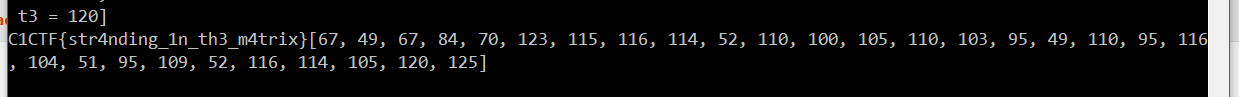
| from z3 import *
FLAG_LEN = 30
sub = [24, 12, 28, 21, 14, 7, 13, 10, 3, 0, 18, 9, 22, 25, 6, 8, 20, 19, 23, 11, 29, 27, 17, 16, 26, 2, 5, 4, 15, 1]
key = b'\xa4r\xa9\xf6\xad\xc2\x11\x18?\xc8\xd01\x01\xd8\xf3\x8cV[8\xce\x9ew\xbb\x179\n\xbaP\x8f\xec_u\xe4Y4\xd0Q\xf0s\x99\x8f\xd1\\\xde4\x8fBZOE=Z\x8bo\x91\xea\x03\xca\xd1C\xf7-6<-_m\x18\x07L\xc48\xf1\x91l\xa7\x01aG\x91\xc5\x0c\xe8\x87\xbc\xb5\xc6\xc7@\xf3%\xa6\x0c\x98"/M\xa1\x80\xaeT#,\xf0\xdc\xb6\xcb#1\x8f\xf5A\x8ap\x10NE\xe69\x0eO\xcaK\x9d\xa9\x06p\\\xba\xa5X\xdf\x82\xe9}\xad\xe3]P\xd7\x7f\xe4\x9b:&\x00\xaa3\xca>x:\xa31\xd2\xcf\xbd\xd2\xf4\xd9\x89\xe9A\xf3G\x89C\x02\xd7\x98=\xed\xd5(\xe2\xdf6fZ\x12\xcbd\xd4 89"\xd0\xdea\xd9\x8eQ&>&f\xc8\xfaX\xf3\xc4V\x13\x83\x97\x88u\x7f\x8a \xa1\xa9\xa3\x0e-\xcf\xe4\xd2\x9a\x85\xed-\\\xe4q\xd9\xbcV\xb3\xe4y\x8c\x83\xddJ\x04V\xf8\xc5g4i\xf6\xc2%\xa1\xc4=\x8a\x828\x8a\xaey\xfbL\xbf\xcer\x96f\xc7,b\xd4U\x81\xd8=\'[k\xee3\xb4B\x03As\x86W\xe1\xa7R\x01\xc3\xbb\xf3\xb4\x14\xfdP\xd9aq\xcfo\xfd\xf9\xc2r\xe6.\x8f\xf8eT\xa8\xde^\xd5\xe0x\xe8\xbcD\xacJR!\xf4>\xa5\xc3V\xe2\xbe8\xab\xf3\x86\xc3R^\xd1\xa5\xce\x14\t\x86\xd5\x11\xb8[\xdd\x0c\x1f\xbd@\x8b\xbb\xc5\x1a\x02\xee\x00\xd0#\xae\xd8\t\x16\xeaa"\xcc\xb2\xea8\x91(\xaek%\xa0]\xc8\x99\xc9\xb9;0eS\xb29\xe4\xfe\x1f\x1d\x8e\x98\xe9\xf6\xc1\x87\xdc\n>\xb8\xb2\xc0\xe2\xca\t\xa0\x0bd\x84\xbekB\x97\xbb\x9b\xfb\x0em\x14e\'\xdc\xfb\x19\xfb>\x96\x84p\xb5\xf1\x9d\x16\xf7\xaa\xbfm\x18\x9d_\x8e\xba\xbd\xc1\x056\x92\x1b\xe8d\xeb\xd014\xd8\x17\x95\x9a6\xbf\xe2\xc3\x8cl\x9c\xca8\x9c\xa2@\x86\xde\xb3sjN\xe9\xb6\xf4\xcfib\xf6\xef\xf6{\x8f\xd0\x03\x85\\C\xd4\x06\xdc7\xe1=\xcd\x9c\xa7\xd6\xef\xbabq\xfb\xacZb?\xcb_+FG\x89@x\xc01\xb8(\x88\x1b^MAM\xe9\xd0\x89\xe2\xd2\xae\xbf\x1d\xa8!\x0c^\x1ci;\xca\x8f1z\xcb\xa94}\xcc\x1b\xf6X\xef\xfd\xfc\x1d\xb4\x96\xd8\xb3\x95\xb4\xbf\x89\x9f\xc3G\xb2\xdc\xccXM\xa0\xfa|!l5\xe6k\x88\xee(0dw\x05n\xbd>\xabl\xc4\x11\x9d,\x7f\xdc/\xecIG\x95\xee\x85X0B\x99\x1b\xe4\xb9\x16_\x01\xb4\xb1\x15)o|60s\x9a\x80\x91\x8f\x12\x993Q\xbd^i\x80\x01\xde\xa9\xfd>7\xf9\xbf\x10\x82\xd4|$\xb7T1\xf2s\xc7\x1a\xa3\xf43\x91\xb8A\xe6e/\xc2\x88$g?x,^\x03\xe9Ff\xf42K\\\xf1\xaci\x98/\x05f"\xb3\xf2\xba\xc2v\x197\x06\x89\'\x96\xa2\xcdQ\xa9>\xfe\x12\x1aj\xab\xfd\xd4\xf8Zx\x04\x1a%\xed\x9c\xd2\x84\xed\x8dz\xbfA"%;3\xdf\x914>\xf4\xf7jl\xd6\x19E\xb4U\xad\r\xcf\x9fJ\x07\x8c\x87\x14aq \xe3v\x84uQz\xd8\xa1*\xc4\xc2\xea\x1bv.\x07\x88\x1f)\x8cD[\x12 \x92]\x9b\xb6\x1fz\x9f\xb4\xf3XI\xe3S\xe0\xc8\xdd\xb5w\xe4\x10Eo\x9f\xf0x\xba\xfd\x13\xcc(Y#\xcfO}\x1f\xde\xf1\xa9\xfc\xee\xee\xf4\x8aD\xff{\x8a\xe9\x7f,(\xb2/g\x84w\x80p\x93|\x87f\xf4\xc1nC)4\x10q\x1fc<\xa0\xdf0\xfa\xb0\xcf{_\xb0\xe5\xc1#\x1a\x0653\xb9\xccJ\x84o\xdc\x1b\xef\xc5m\x18>b\x03<"\x803 \x13)\x9e\x94)\xce'
enc = [12, 115, 141, 48, 115, 115, 121, 96, 85, 91, 115, 187, 28, 42, 62, 40, 200, 95, 192, 112, 15, 17, 75, 173, 123, 243, 156, 32, 182, 222]
tmp = [BitVec('tmp%d' % i, 8) for i in range(FLAG_LEN)]
matrixA = []
for i in range(FLAG_LEN):
line = [0] * FLAG_LEN
for j in range(FLAG_LEN):
line[j] = key[FLAG_LEN * j + i]
matrixA.append(line)
solver = Solver()
for i in range(FLAG_LEN):
sum = 0
for j in range(FLAG_LEN):
sum = (sum + ((tmp[j] * matrixA[i][j]) % 256)) % 256
solver.add(sum == enc[i])
if solver.check() != sat:
raise RuntimeError()
m = solver.model()
print(solver.model())
flag = ""
for i in range(FLAG_LEN):
tmp[i] = m[tmp[i]].as_long().real
flag = [0] * 30
for i in range(30):
flag[sub[i]] = tmp[i]
for i in range(30):
print(chr(flag[i]), end="")
|